
Content-ID™
High-Performance Threat Prevention
Enterprise networks are rife with applications that can evade detection. Common methods include dynamically hopping ports, re-using other ports, emulating other applications or tunneling inside SSL. The use of evasive applications has not gone unnoticed by attackers as they increasingly use these invisible applications to transport threats past the firewall. Content-ID melds a uniform threat signature format, stream-based scanning and a comprehensive URL database with elements of application visibility to detect and block a wide range of threats, control non-work related web surfing, and limit unauthorized file and data transfers.
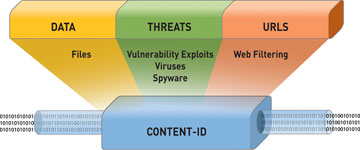
Content-ID gives you a real-time threat prevention engine, combined with a comprehensive URL database, and elements of application identification to:
- Limit unauthorized data and file transfers
- Detect and block exploits, malware and malware communications
- Control unapproved web surfing
The application visibility and control of App-ID, coupled with the content inspection enabled by Content-ID, empowers your IT team to regain control over your application traffic and related content.
Integrated IPS and Anti-Malware
Content-ID provides you with fully integrated protection from vulnerability exploits, malware and malware generated command-and-control traffic. As with all Palo Alto Networks analysis, threat prevention is applied in full application and protocol context - across all your traffic and ports - to ensure that threats are detected and blocked, despite evasion attempts. Our threat prevention technologies include:
- IPS - IPS functionality blocks vulnerability exploits, buffer overflows, DoS attacks and port scans. Additional capabilities, like blocking invalid or malformed packets, IP defragmentation and TCP reassembly, protect you from the evasion and obfuscation methods used by attackers.
- Stream-Based Network Antivirus - Palo Alto Networks maintains a database of more than 15 million samples of malware. Every day we analyze an additional 50,000 samples. Malware is detected by a stream-based engine that blocks in-line at very high speeds. Malware enforcement is available to you across a variety of protocols including HTTP, SMTP, IMAP, POP3, FTP and SMB.
- Anti-Spyware – In addition to controlling viruses and malware, Content-ID stops spyware and malware communications including:
- Botnet communications
- Browser hijacks
- Adware
- Backdoor behavior
- Keyloggers
- Data theft
- Net-worms
- Peer-to-peer traffic
Our Anti-Spyware also passively analyzes DNS queries to identify the unique patterns of botnets. This reveals infected users and prevents data from leaving your enterprise.
URL Filtering
Our fully integrated URL filtering database lets you more easily and effectively enforce your policies for web browsing, which complements the policy-based application visibility and control delivered by our next-generation firewalls. Tie your URL filtering visibility and policy controls to specific users through transparent integration with enterprise directory services like Active Directory, LDAP and eDirectory. You can gain even more insight into your URL filtering by generating customizable reports and through log analysis.
- Securely enable web usage with the same policy control mechanisms that you apply to applications – allow, allow and scan, apply QoS, block and more.
- Reduce malware incidents by blocking access to known malware and phishing download sites.
- Tailor your web filtering control efforts by creating white lists (allow), black lists (block), or through custom categories and database customization.
- Facilitate and hone your SSL decryption policies. For example, “don’t decrypt traffic to financial services sites,” but “decrypt traffic to blog sites."
File and Data Filtering
The data filtering features in Content-ID enable you to implement policies that reduce the risks associated with the transfer of unauthorized files and data.
- File blocking by type: Control the flow of a wide range of file types by looking deep within the payload to identify the file type (as opposed to looking only at the file extension).
- Data filtering: Control the transfer of sensitive data patterns such as credit card and social security numbers in application content or attachments.
- File transfer function control: Control file transfer functionality within an individual application, allowing application use while preventing undesired inbound or outbound file transfers.
